Goto Fail
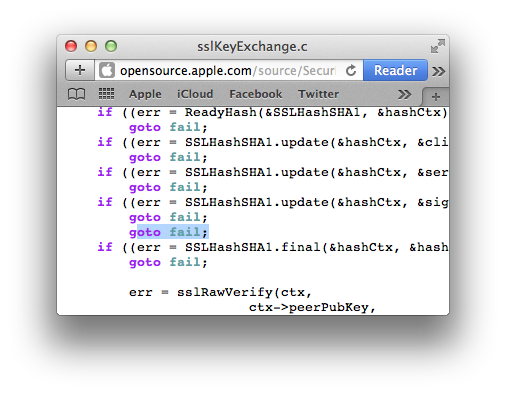
Now that the media frenzy over Apple's SSL (goto fail) MitM vulnerability has calmed and our iPhones and Macs have been updated, folks are starting to reflect. That's a good thing. Among other things, this event has pushed issues of code quality, review, testing, patching/updates, version blocking and user notification up the management chain to, hopefully, get more focus and funding.
This had something for everyone and the net is now flooded with commentary on it. I'm certainly not going to repeat that, but consider:
- Some static analyzers (like Coverity and clang with -Wunreachable-code) would have caught this.
- Peer code review likely would have caught this.
- The bug was in the open source community for anyone to find.
- Vendors everywhere were asking how they could help notify their users and ensure they upgrade.
This one-liner joins the ranks of the most apt and pithy software bugs. It's right up there with the misplaced break that broke the AT&T network on my 25th birthday. BTW, if your birthday call to me didn't get through that day, there's still time; call or message me. But please upgrade your iPhone first.